This document describes the actions that the system performs when you suspend an account.
Note:
To suspend or unsuspend an account, use WHM’s Manage Account Suspension interface (WHM >> Home >> Account Functions >> Manage Account Suspension).
The following table describes the actions that the system performs when you suspend an account and the limitations that result from these actions:
Note:
In the following section, user represents the account’s username.
The system adds the SUSPENDED=1 and SUSPENDTIME=epochdate flags to the account’s /var/cpanel/users/cpuser file, where epochdate represents the Unix time at which you suspended the account.
As a result, the appropriate WHM interface sets the account to suspended and lists the reason for suspension.
If you select the Prevent resellers from unsuspending checkbox when you suspend the account, the system touches the /var/cpanel/suspended/user.lock file.
As a result, the appropriate WHM interface sets the account to locked. The system does not allow resellers to unsuspend the account.
Warning:
If you select this option when you suspend an account, the system only allows the root user to unsuspend the account.
The system stops all of the processes that that account owns.
As a result, the system stops any functions that the cPanel account currently performs as the logged-in user.
The following list includes some of the effects that this action may cause:
– The system forcibly logs the user out of a current session.
– The system stops the user’s cron jobs.
The system creates a suspended.lists directory in Mailman and moves the files for each of the account’s mailing lists to this directory.
As a result, the account’s mailing lists no longer function.
The system creates a /etc/webdav/shadow directory in the user’s home directory.
As a result, the account’s Web Disk accounts no longer function.
The system adds LOCKED string to the /etc/shadow password files for all of the account’s email users.
As a result, the account’s email users cannot download mail.
Note:
The system continues to deliver mail to the account.
The system no longer allows the account’s users to send email through the mail server.
Also, the mail server will force all mail currently in the outbound message queue from that account’s users to fail.
As a result, the account’s email users cannot send mail, and any mail they had in the mail server queue will fail.
The system updates Apache’s httpd.conf file with a Virtual Host include file for the user.
– The system creates the include file at the following location:
![]()
– This include file contains a RedirectMatch rule that redirects website traffic to the default template for suspended accounts.
Note:
Apache httpd.conf include files originate from the following lines in Apache’s main.default file:
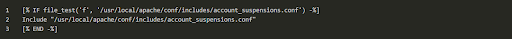
As a result, visitors cannot access the account’s websites. Instead, a message appears that states the account was suspended.
Note:
To edit the message that appears for a suspended account’s sites, use WHM’s Web Template Editor interface (WHM >> Home >> Account Functions >> Web Template Editor).
The system uses the passwd -l command to lock the account’s /etc/shadow password file. This command prepends the account’s passwords with two exclamation marks (!!).
The following list includes some of the effects that this action causes:
– The user cannot log in to their cPanel account.
– The account’s database users cannot log in to their databases.
– The suspended account’s password cannot change.
The system modifies the permissions of the user’s public_ftp directory to 0000.
The system then creates the /etc/proftpd/user.suspended file and locks the account’s FTP passwords in the /etc/proftpd/passwd.vhosts and /etc/proftpd/user password files. Finally, the system prepends the account’s FTP passwords with two exclamation marks ( !! ).
As a result, The account’s FTP users cannot log in to the FTP server.
Also, the system cannot back up the user’s public_ftp directory because of the restrictive file permissions.
The system changes all of the MySQL users’ passwords. As a result, MySQL users cannot access their databases.